Today we’re writing about money, and we think you’ll find the angle quite interesting. Instead of an “earning ’em” story, we’re giving you a “gettin ’em” story. We’ll guide you through the recent changes in the European regulatory framework for online payments and secure customer authentication (SCA), then offer you a history of the existing and (possibly) future online payment solutions. After that, you’ll find out what you should (and shouldn’t) do if you’re a PortaBilling customer. And there is a bit of intermingling between an ordinary life and the global intersection of commerce, technology, and human history at the very end of this story.
A long time ago (2007, that is), the European Commission (EC) adopted its Payment Services Directive (PSD1) on behalf of the SEPA (Single Euro Payments Area). It was revolutionary for its time, and, ironically, it enabled Amazon, Apple, Google, and the likes to easily conquer Europe. This made life more difficult for local digital entrepreneurs, a discontent that culminated with the EU startup revolt of November 2020. The other side’s opinion is that the market is the market and that customers should be the ones to make their choices, not the European Commission. (Also: that it’s not a fault – but, rather, a feature – of the Silicon Valley giants, whose services are useful and handy.)
PSD2 and Payment Service Providers
In 2013 the EC conducted research on how its creation (i.e., PSD1) “was doing.” The research report did the work of helping them feel proud of themselves, but it also noticed “third party payment service providers” – a business model that had turned PayPal, Braintree, Square, Stripe, ChargeBee, Transferwise, and others into multi-million-dollar companies.
Payment providers appeared as an additional intermediary between the customer’s bank and the merchant receiving the payment. These new players provide an additional layer of convenience to the merchant and the end customer while also creating additional security drama for the issuing bank and the payment systems (or “payment solutions,” as they prefer to call themselves) serving the transaction.
PSD2 Novelties
Of course, the EC was happy to regulate additional ecosystem participants.😉 Hence, PSD2 appeared in 2015. Among its numerous novelties, there are two that are important for the purposes of this story.
Firstly, PSD2 extends its regulatory framework to countries outside the EU, thus enabling open banking: several APIs that facilitate data interchange between banks, payment providers, and various compliance agencies. Secondly, PSD2’s Article 4(30) introduces the term “strong customer authentication.” Mastercard did a great job of summarizing and explaining the concept in 2018. This is ironic because, back in 2011, Visa was an early adopter of 3D Secure, a technology dubbed “the main method for authenticating online card payments and meeting the new SCA requirements” by Stripe – second only to PayPal in the online payments kingdom.
SCA, 3D Secure, Google Pay, Apple Pay, NameYourOwn Pay
Even without throwing in the scary numbers that demonstrate Internet credit and debit card fraud, it’s evident that it’s a big issue for the banking system. In fact, early attempts to do something about it date back to 1984. That date may make it sound like George Orwell’s novel, but it’s not that scary! Since then, most of the efforts in this direction evolved around some other authentication factor besides the document (digital certificate, database entry) that identifies the individual or the transaction. The “Knows-Has-Is” triad has also been around for quite some time. However, some major developments have occurred since the PSD1.
“Knows” (Passwords and Passcodes)
3D Secure, sometimes shortened to 3DS (please do not confuse it with the legendary game console by Nintendo discontinued this year), is the SCA’s poster child. Nevertheless, it is by far not the only authentication solution available out there. 3DS is over 20 years old. Sunnyvale-based Arcot Systems originally developed it back in 1999. 3DS then ended up being part of Broadcom’s patent portfolio after a chain of M&A transactions.
It’s Usability, Folks!
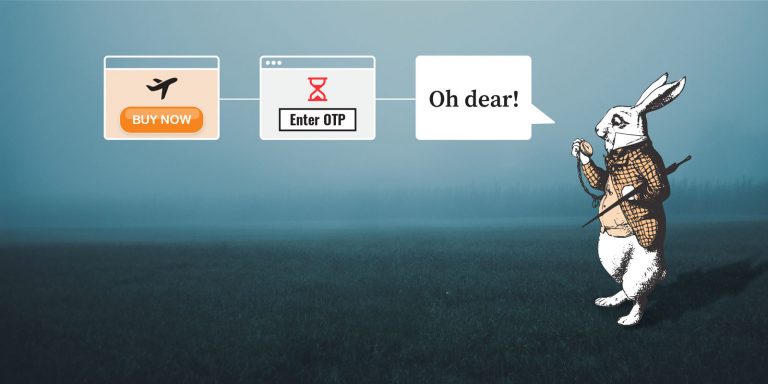
Have you ever ended up on a stressful landing page where you were forced to try to prove your identity while shopping online? Banks call this a “challenge page.” Often, it causes a shopper to panic and abandon their shopping. Why? Because it’s set up like this:
- It looks totally different from the UI of the website you are shopping on. (“Is this fraud?” your mind likely signals.)
- It gives you three or so minutes to receive and type in a 6 or 8 digit code. And this code comes as an SMS or push notification from your bank’s smartphone app. BTW, if the idea of “three minutes” made you laugh because your relationship with your mobile carrier is akin to that of John Oliver and AT&T – we totally empathize with you.
- If you miss that three-minute deadline or enter the code wrong, you get a notification basically saying: Bad luck, friend, you are now timed out. Now go and repeat all that ordeal again.
And that, in a nutshell, is 3DS, Version 1. 😂
There were some updates to 3DS throughout its 30-year history. However, the “get a message with the code and type it in” song stayed the same. Some relief came in the late 2010s with Google’s SMS Retriever API for Android and Apple’s AutoFill for iOS. Both features allow developers of apps approved by Google or Apple to read the SMS and autofill the OTP (“one-time password” – not the Hungarian bank) on the challenge page.
Banks and mobile developers now widely use this functionality to simplify the SCA workflow for customers. (Though there might be changes for Chrome customers soon after Google upgrades WebOTP to public release from the experimental feature.)
3DS v.2, Risk-based Authentication and Why It Is Good News to Everyone
Currently, the implementation process for 3DS is governed by EMVCo – an interoperability body supported by all the major payment systems. Obviously, neither banks nor payment systems were happy with the usability issues of 3DS. In 2019 a report stated that 22% of transactions involving 3DS ended up with customers walking away without completing the purchase. A response from EMVCo came in the form of a technology dubbed “3D Secure. Version 2.0.” (Wait, is the “two-point-oh” thing a gimmick from the early ’00s?)
The most important innovation of 3DS v.2 is risk-based authentication (RBA). Visa claims this feature will allow 95% of customers to bypass the scary challenge page. RBA achieves that by applying machine learning instruments to each transaction and considering various factors, such as transaction cost, previous purchases involving the same parties, and various pieces of customer information (device, software, transaction, and behavioral history).
3DS v.2 is also natively mobile-friendly, while v.1 was conceived before smartphones reached the mass market. It also enables out-of-band authentication, which is helpful in high-risk situations.
“Is” (Biometrics)
Here, most people know about Touch ID and Face ID. As is the case with most Apple products, these technologies were not the first on the market. But, as is also the case with most Apple products, they did reinvent the UI and make these features very customer-friendly. This might not always be true with Touch ID, but that’s a problem of human finger capillaries and the current state of finger scanning technology. Besides facial recognition, which Apple acquired together with Israel-based PrimeSense, there is also eye-vein verification (since the 1990s), which was pioneered by EyeVerify and its Kansas-based professor and founder Reza Derakhshani. In 2016, Alibaba acquired EyeVerify for $100 million.
“Has” (Devices and Hardware Tokens)
The Knows-Has-Is triad is the professor’s pet for any cryptography or information security class, and it works perfectly as a Thanksgiving dinner table explainer. However, an engineer or entrepreneur with experience in the area of cybersecurity will tell you that, for a long time, it has been all “Has” and little “Knows” or “Is.” Why? Any passcode or passphrase has to be sent to the verifying party via some kind of device. And any biometric information needs to be acquired from the user using some kind of sensor (camera, microphone, scanner, etc.).
Standalone tokens are great, and some even gained widespread market adoption. There is FIDO Alliance, an industry organization championing standalone hardware second-factor devices and administering the U2F standard for them. FIDO Alliance members include Google, Facebook, and GitHub.
However, let’s be frank here: unless you’re a Bitcoin aficionado or a developer running a multi-million-dollar code (and one who’s paranoid about anybody else having access to your bugs and features), why would you need an additional gadget? Particularly one that is so secure that losing it might actually lock you out?
This leaves us with Google, Apple, and (to some extent) Microsoft.
CDCVM as an SCA Alternative
Consumer Device Cardholder Verification Method (CDCVM) allows mobile devices (smartphones, tablets, and smartwatches) to conduct PINless customer verification. It has “bipartisan” support from both Apple and Google. And guess who runs CDVCM on behalf of the payment systems? The same EMVCo that runs 3DS. However, in light of the Apple Card launch of 2019 and news of leaked Google plans to launch one as well, the future of the partnership between established payment systems (Mastercard, Visa, etc.) and mobile device vendors does not look optimistic at all.
Proprietary risk calculation algorithms are the ultimate market entry barrier that helps the established payment systems stay in business. However, given Apple and Google’s relationship with machine learning, this barrier won’t last longer than the expiry dates for the key patents owned by Mastercard and Visa.
To make things even more complicated for the payment systems and banks, device vendors got an unexpected ally in this standoff… and it’s COVID. Who wants to touch physical payment cards when you can just tap on the sensor with your phone or smartwatch? While it doesn’t look like Big Tech will be your next banker anytime soon, they are definitely cutting their teeth on the retail payments business. We forecast that there will be no 3DS v.3. This unnecessary intermediary will die of natural causes: the device vendors’ willingness to control their users’ experience and the banks’ willingness to pay less commission per payment. But for now: let’s return to SCA and implementation of 3DS v.2.
Deadlines Are (Not) SCA’s Best Friends
Not all market participants were happy with the new SCA requirements. Unexpectedly, in 2016, Visa, the very same early adopter of 3DS back in 2001, was among the first key market players to criticize the European mandatory approach to SCA. Stripe went even further and commissioned research that forecast a €57-billion loss to Europe’s e-commerce within the first 12 months after the SCA requirement came into effect. Later the European hospitality industry joined the public outcry, stating that the lockdown is already killing them enough. The European Banking Authority (EBA) fought back with various opinions and statements. Finally, EBA yielded to pressure and published a recommendation that the deadline should be postponed. Most, but not all, countries agreed to December 31, 2020, as the new deadline. Once again, Stripe did a great job explaining the cascade of SCA enforcement dates, depending on the cardholder’s residency and the country of the bank that issued the card.
What Does SCA Mean To You?
If you are a CSP based in Europe and want to charge for your service to a customer who has a credit card issued by a bank in the EU, you will not be able to do so after January 1, 2021 – unless you have SCA in place! chances are this SCA thing will drastically impact your cash flow. And unless you are a “total privacy” operator, providing anonymous registration, fully encrypted calls, and payment for the service in cryptocurrency (yes, you can do this with PortaSwitch as well) or you are an operator of a call shop – a place where migrant workers come to call home from a phone booth and pay with cash (definitely a future blog story) – chances are this SCA thing will drastically impact your cash flow.
PortaBilling, SCA and Stripe to the Rescue
There’s good news if you’re already using PortaBilling:
- We implemented the most recent version of Stripe’s payment APIs to make you SCA ready. And even better: you don’t have to upgrade to the most recent MR. Our iPaaS technology will allow you simply to use the cloud service and the relevant container.
- We are making all possible efforts for your transactions to fall under one of the SCA exemptions. This means your customers won’t see the challenge page in most cases.
- Stripe (and our new implementation of its APIs) already supports Apple Pay and Google Pay. What this means is that, when the Great Payments War for the End Customer erupts between payment systems and device vendors, you will be safe on both sides, just like Missouri. An important caveat here: SCA-compliant payments are available within the PortaSwitch self-care portal, off the shelf. If you need this functionality on your custom-coded portal, you will be responsible for the necessary adjustments.
- We are not limiting ourselves only to Stripe. If you want to request an integration with a different payment system, please connect with our customer service team. Since PortaBilling infrastructure already supports SCA compliant payments, adding another payment system is much simpler now.
An Authentication That Is Not Scary: Yuliia’s Story
“In my childhood, programmers and IT folk in general were some kind of supersmart aliens from another world. I never thought I would grow up to become one,” says Yuliia Vorchak, a developer at PortaOne. Yuliia joined us in 2015 as a support engineer, after working as a coder at a different company. Three years ago, she was promoted to software engineer and rejoined the developer ranks again. “I started with TurboPascal like any other post-Soviet schoolkid,” she says. “Then it was Java. Now it’s Perl.” Together with her team Yuliia brought the new PortaBilling payments architecture to life, and implemented the new version of Stripe API that supports SCA.
Yuliia’s own first online payment was in 2014, when she bought some cosmetics online. “That was chilling quite a bit,” she remembers. “But that’s when the ‘you’re a girl’ stereotype worked. I saw the item. I really wanted it. And then it was all as if in a fog.”
But online commerce wasn’t always a smooth experience for Yuliia. “That was for a New Year’s Eve party [called ‘corporativ’ in our part of the world]. I bought a costume. And it was totally an illustration of the ‘expectation vs. reality’ Internet meme. I still decided to go, but without a costume. After all, it’s the confidence that really matters, not an outfit.”
The EU, the SEPA, and the “Scary Moment”
Yuliia managed to make her first trip to the EU before the lockdown. “It was a bus tour via Poland, Germany, the Netherlands, Belgium, and the Czech Republic,” she says. “The bus looked and felt super cozy… At first. I hardly even remember Amsterdam because I desperately wanted to sleep. After several nights of sleeping on a bus, you’re just dreaming of a decent bed. But it was all worth it. We bought my first euros at an exchange booth somewhere in Germany. It wasn’t a big deal. We just needed cash to buy food and things.”
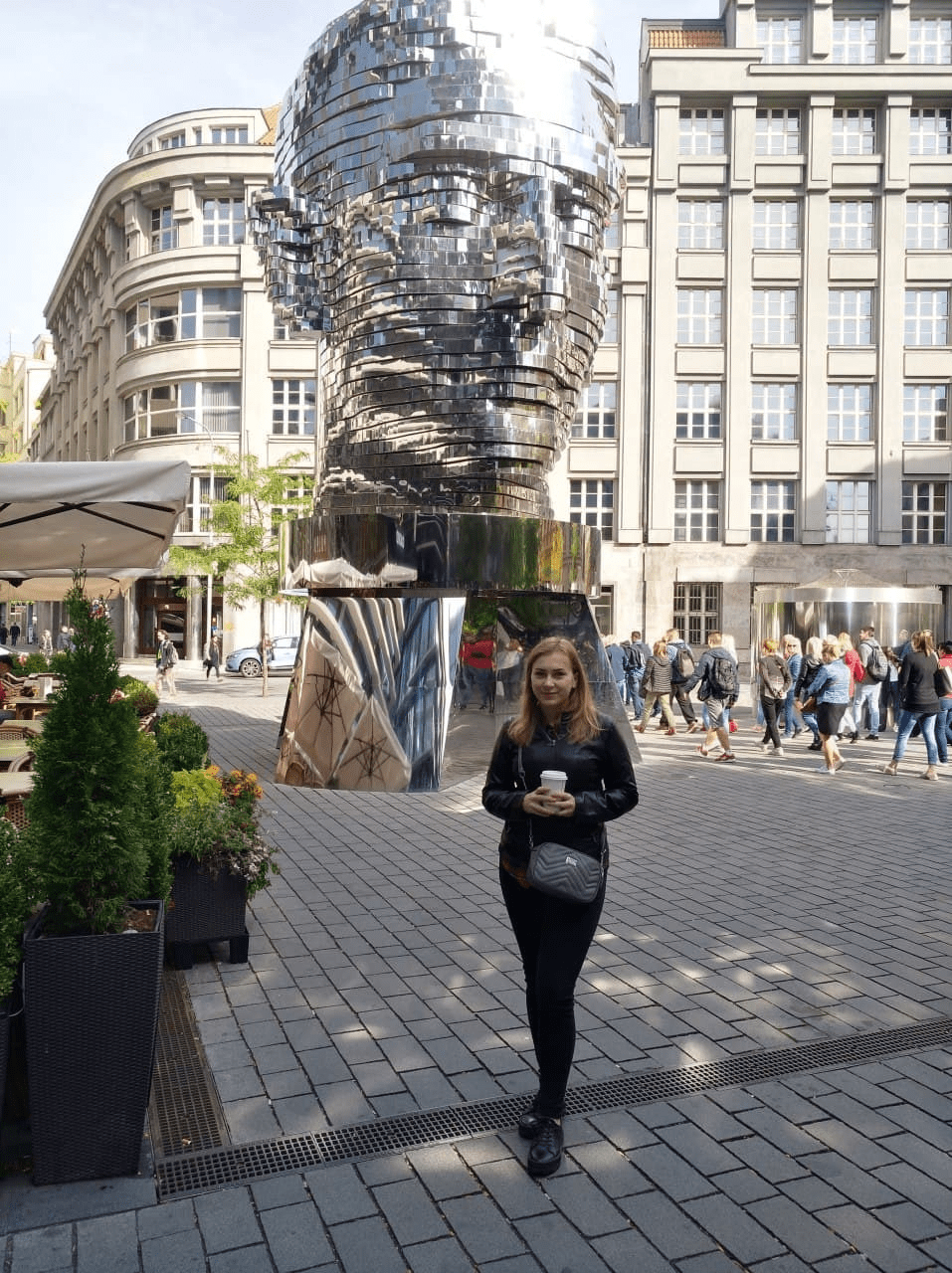
“The scariest experience came at a border crossing from the EU back into Ukraine. It was midnight. Two officers entered the bus to check our IDs. Probably they liked us, two young girls, and decided to play a joke. One was checking my papers, making a thorough look. The other was checking my friend’s, and she turned totally pale. Then they smiled and walked away. But there was a moment when I really believed they would take us with them for some interrogation. It was scary,” she recalls.
“I would love to return to Europe after the lockdown. Probably to Amsterdam or the Hague. From 2015 to 2017, the major client I was supporting was located in the Netherlands. During the bus trip last year, a guide instructed us not to get lost in the Dutch subway. One group got lost in Amsterdam. They ended up in Rotterdam.”
And here’s a coincidence you may find interesting (if you find coincidences interesting, that is): today, Yuliia is making authentication instruments that are definitely not scary—and won’t make you feel lost.